

It’s no small task to safeguard our security and privacy online. While new technologies and the internet make our lives easier and better connected, they also open doors for undesirable elements like online crime and mass surveillance. As we produce more and more digital information, it becomes both increasingly important and increasingly difficult to manage our data, control access to them and protect them from unwanted intruders.
TL;DR: Privacy and security online matter. This toolbox provides a starting point to protect them. For our favorite tools and advice, download our quick tips.
Most of us face the following dilemma: we do not want companies and governments to dig into our online lives, but we also cannot afford to go offline completely, nor do we want to invest the time needed to specialize in these issues. We should realize, however, that it is still possible to take measures to protect our data online.
If you are curious about online privacy and security, but do not consider yourself a technology expert, this toolbox – a basic primer on maintaining online privacy and security – is for you. It is easy to digest and non-technical in nature, intended for anyone of basic familiarity with computers. This text offers first practical steps towards greater online privacy, explains key concepts and points to resources with more-detailed instructions. The tools and tricks described on this website are quick and effective. Unfortunately, “perfect” digital security is impossible to achieve, given the internet’s core architecture, but it is certainly possible to improve your digital self-determination.
In the view of the authors, this toolbox is a starting point at best. We recognize that many new technologies deliver tools that are practical and even capable of enhancing privacy. Nevertheless, we believe that most internet users can become better-informed netizens. So long as digital security remains the responsibility of the end user, we hope that more tools and discussions aimed at achieving digital security emerge.
The authors of this toolbox are aficionados of privacy and digital security issues. We were inspired to create this guide when our friends and colleagues began asking us why our browsers have so many add-ons and why our WiFi passwords are so long and cryptic. We quickly realized that despite the apparent interest in bolstering information security, there was an absence of user-friendly manuals for doing so. The result is this guide, which we consider an evolving and living document. If you love using the internet, but worry about how it’s using you and your data in return, then you’re in the right place.
This guide is indebted to the work of Front Line Defenders and the Tactical Technology Collective’s Security in-a-Box, the Digital Defenders Project’s Digital First Aid, the Electronic Frontier Foundation’s (EFF) Surveillance Self-Defense and the Freedom of the Press Foundation’s Encryption Works.
We invite you to send us any comments or feedback.
Sure, you probably have nothing to hide. But let’s challenge this idea, which implies that only those involved in illegal activity should worry about maintaining their privacy. Privacy is not about hiding. Would you hand out lists of your credit card transactions? Would you ever take down all the curtains in your home? Protecting personal data is about protecting your personal space in order to allow the independent and unhindered development of yourself and your thoughts.
Your data, stored en masse or stolen, can be incredibly revealing. Your data paint a vivid picture of what you're interested in, whom you connect with, the things you're willing to pay money for, where you go and even how you think. If you cannot control or even know who accesses all of this information, you are giving up substantial power to intruders.
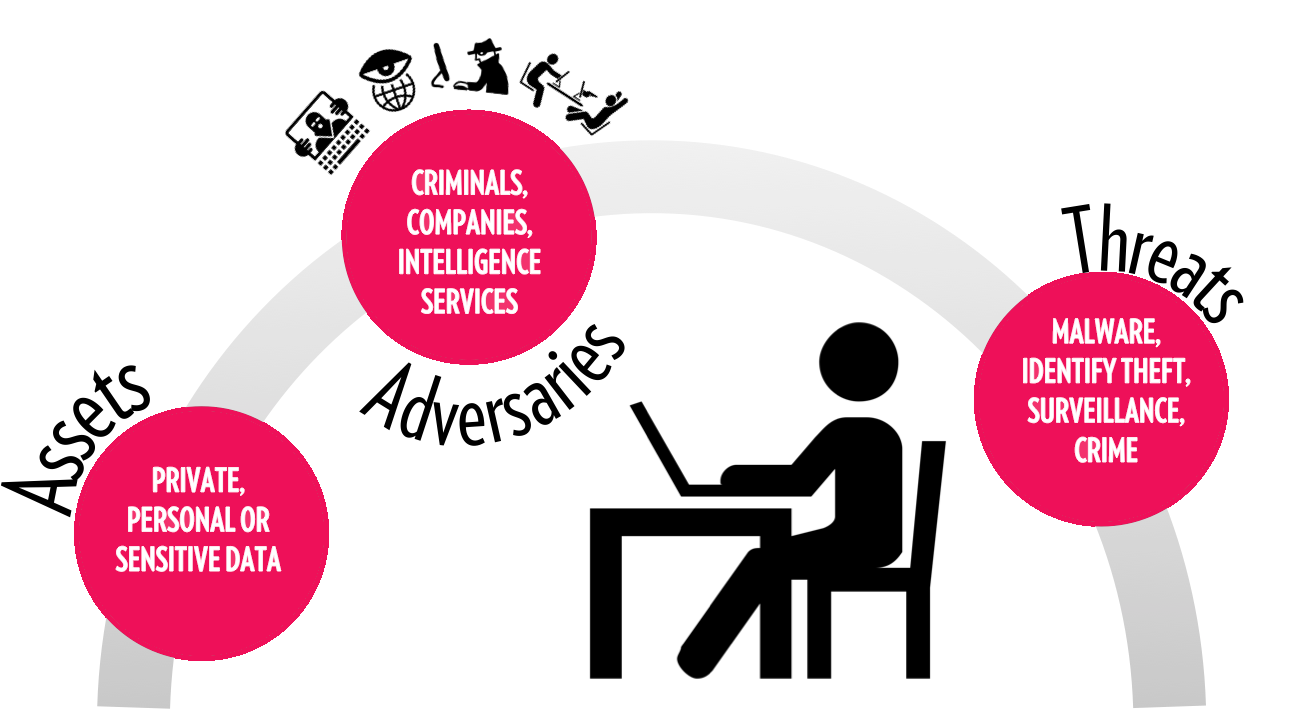
We all have different priorities when it comes to online privacy. To decide what matters most to you, you can apply a threat model to identify your primary assets and threats – that is, data or information you want to protect, and the ways in which they could be compromised. Upon doing so, you can determine the likelihood and potential consequences of these assets being compromised.
The threats we face online range from organized crime and identity theft, to malware and subtle data collection. These threats usually stem from one of three main actors that gather or gain access to your data without letting you know or giving you a choice: cybercriminals, government agencies and private companies (often advertisers).
This guide recognizes that different threats require different solutions, and that people are willing to invest varying degrees of effort in online privacy and security. You yourself are the best judge of how much time to invest, and you should use the tools proposed in the next few sections to fit your specific needs.

Aha-moments in five minutes:
To gain an initial overview of who might be prying into your online activity, use Trackography. It visualizes the actors that track you when you visit news websites and that know, as a result, which articles you click on, how long you look at them and which links you follow.
The Mozilla Lightbeam add-on provides an even more personal overview of how “you’re being watched” by mapping your watchers. The result is a mind-boggling web of trackers. In all likelihood, you’ve never heard of the companies behind these trackers, so do find out how much they know about you.
Being tracked online is not exactly “bad.” In many ways, these trackers are critical to tailoring and customizing online services: a tracker that knows the websites you visit and what you do there can offer more personalized recommendations. In return, these trackers receive detailed profiles of your likings, which they can sell to advertisers.
Online tracking is part of the backbone of most of today’s online business models. Many services are offered for “free,” in exchange for data that allows companies and website hosts to tailor advertisements to increase their sales elsewhere.
If you want to prevent third parties from tracking you, it helps to understand how they work. One key enabling piece is a browser cookie: “a small file, saved on your computer by your browser that can be used to store information for, or identify you to, a particular website.” It associates your previous activity on a given website in exchange for convenience, such as faster loading speed, personalized content and permanent log-in. But there is a downside: cookies have long been complicit in privacy infringement by making browsing history available to advertisers.
If you are bothered by the idea of hidden trackers watching you visit the web, there are a few tools at your disposal. We propose two steps: prevention and re-routing.
Immediate effectiveness within seconds:
Privacy-enhancing tools often come as plugins or add-ons, which are lightweight programs that operate within your web browser once they have been downloaded and installed. In a way, they are like gadgets you might add to a car or bike (radios, GPS, alarm system): they allow you to customize your gateway to the internet.
The plugins Disconnect.me and Privacy Badger offer a simple and efficient start to blocking trackers. Try the aforementioned Lightbeam before and after installing the tools to observe the difference they make. Disconnect.me, created by a group of lawyers and former Google employees, is a free, open-source add-on that allows you to visualize and block a variety of third-party trackers. Privacy Badger was developed by the Electronic Frontier Foundation (EFF) to catch trackers that sneak past other tools. These include Ghostery and Blur, which you can install as complementary extra shields.
In addition, all major browsers allow you to turn on a do-not-track-feature that asks companies not to track you. Note, however, that there is no enforcement mechanism, so you should complement this first step with additional add-ons and tools.
Another kind of blocking is disabling ad displays. Ads are not only annoying, but can also deliver malware. To disable these displays, install ad blockers, such as Adblock Edge, AdGuard or uBlock. With a bit of a different approach, Adnauseam obfuscates your browsing data by literally clicking on each and every advertisement that it finds.
Finally, the plugins NoScript (Firefox) and ScriptSafe (Chrome) allow you to disable JavaScript, a scripting programming language that enables not only the functioning of many websites, but also the execution of potentially malicious or unwanted scripts, such as social media buttons. Be aware that the add-ons can render some websites useless, but you can always whitelist individual websites.
It is recommended that you install and automatically run several of these add-ons simultaneously, as each one targets different types of trackers. Whichever you choose, be sure to install them for all of the browsers you use.
In fact, using different browsers for different activities can help to prevent tracking, as no tracker can follow you into separate software. If you do not trust the blockers mentioned above and want to prevent Facebook from watching your activities on webpages that are open on a separate tab, consider assigning specific uses to specific browsers, e.g., use Facebook in Chrome and browse the web in Firefox. You can find more information here on advanced browsing strategies.
In any case, it is good practice to log out of every service at the end of a session. You can do so by setting your browser to automatically delete local cookies after each browsing session. Be aware, though, that you will then need to log into your email client or social media account every time you start your browser.
Finally, some companies have come together in the Digital Advertising Alliance and taken steps to increase their transparency and give users the chance to opt out from “interest-based” advertising on their websites. The guide “Your Online Choices” is worth a look, as it offers further explanation on online behavioral advertising and adjusting tracking preferences.

Online lifestyle changes, simplified:
While certain companies might make money with your data, they pale in comparison with more malicious actors, who might be after your passwords, bank accounts or identity. A number of security tools can help channel your online activities through routes that are more secure.
First, you should install the HTTPS Everywhere browser extension. The “http://” that comes at the start of web addresses is revealing of a protocol that makes sure that websites and browsers know how to connect to each other. The “s” that is sometimes included in this part of a web address stands for “secure”; it means that the path for the connection in question is more secure because it uses SSL/TLS encryption.
Encryption, by the way, is a technical solution that encodes your data traffic so as to make it legible only to those who hold a key. You do not always have to hold this key yourself, but sometimes you implicitly grant it to the browser you use. To make basic network encryption obvious to you, your browser will typically show a little lock symbol.
HTTPS essentially forces your browser to use only secure connections, when available. This is especially important for websites that require sensitive information (e.g., username, email address, password). Another useful tool to that end is the Firefox add-on PassSec, which automatically warns you about insecure password fields.
Another way to avoid insecure channels is to use Virtual Private Networks (VPN). VPNs route your online traffic through a separate network before sending it to the intended destination. VPN providers encrypt the data you send and receive, helping you to bypass insecure public internet connections and hiding your IP address. If you work on your laptop from a café with public WiFi, a VPN would be useful, unless you want your unencrypted traffic as well as your metadata to be an open book for your barista.
Most VPN providers give you the option of choosing a country that you want to be routed through – a feature enjoyed by those of us annoyed by blocked content on YouTube and Netflix in some countries. Here is a longer explanation of a VPN’s advantages as well as a rating of providers, based on factors such as whether a VPN keeps logs or the jurisdiction under which it falls. Notably, VPN security comes with a literal price: most providers charge for their services. In addition, it does not protect you from being tracked or from the downloading of malware when visiting a dubious website.
In addition, there is a caveat to sending all of your online traffic through channels that are selected and encrypted, and thus overseen and controlled by the VPN provider. Your browsing history may be hidden from companies and spying agencies, but a single entity, the VPN, could theoretically review all of it. Most VPNs are unlikely to do that, since their business depends on guaranteeing privacy, but it’s nevertheless an uncertain affair. Therefore, it is important to carefully review any service you plan to sign up for.
A more advanced, though simple, method of enhancing your privacy online is offered by the Tor Project, mostly known for its web browser. It allows you to browse the internet anonymously by routing your web request through a number of different relays. Originally created by the US government to protect government communications, it is now widely used to establish enhanced privacy (often from the US government) through a distributed, anonymous network of servers.
Tor may be the best tool for guaranteeing anonymity, by protecting you from government and private company surveillance. On the downside, the Tor browser can add occasional annoyances to your online navigation: it blocks certain services, and sites can take longer to load.
The ultimate method for enhancing your privacy online is offered by the Tor Project, mostly known for its web browser. Originally created by the US government to protect government communications, it is now widely used to establish enhanced privacy (often from the US government) through a distributed, anonymous network of servers. It may be the best bet against tracking, as the other methods above cannot completely evade and block the pervasive ad cookies. In general, Tor is a great tool for staying anonymous online. On the downside, the Tor web browser can make it harder for you to navigate online: it blocks certain services, and sites can sometimes take longer to load. Options that operate in a similar fashion but are slightly more user-friendly include the whitehat web browser and Anonymouse. The latter you access in your regular browser, type in the homepage you want to access, and you will be redirected there anonymously.
Not all data is taken without our permission. In fact, we often opt in, knowingly or unknowingly, to “pay” for useful and convenient services – like apps and social media platforms – with our personal data. Two approaches can help protect your personal data.
First, data minimization refers to the idea that you reduce the amount of data that you give away (and that can be stolen or compromised as a result). Second, you can diversify the services you use in order to avoid pooling all of your information with one provider or to intentionally obfuscate your behavior.
More control through exploration:
To reduce the data you share, you should become aware of what you have shared in the past. While you might not choose to leave behind the biggest trackers, such as Facebook and Google, we recommend that you at least become more aware of the type of information you are giving away.
Facebook, for instance, allows you to download some of the information that it has saved about you. Similarly, Twitter allows you to download your archive. Google offers even more options: you can “takeout” information about you and control what Google saves about you in your dashboard.
If using any online services, make sure you catch low-hanging fruit by controlling your privacy settings.
It can be mind-boggling to see just how much information online tools collect and keep about us without our realizing it. If you want to know how much Google has learned about your relationships with friends and colleagues, take a look at Immersion, a free tool that extracts and graphically maps your social network. You should also review the other apps that you (perhaps unknowingly) have granted permission to access your Google data. Here are more tools for finding out what Google knows about you.
The rise of social media and “free” online tools that we pay for with our data pose a common quandary. On the one hand, services like Google and Facebook are immensely helpful and convenient. On the other hand, they collect potentially sensitive data about us. It may be impossible to truly know how much these sites actually know about us, or how they use that information – yet they have our full permission.
Many online contradictions result from what is perhaps the biggest lie that we often tell on the internet: clicking the “I read – and agree with – the terms of services” button. One click, and we end up signing agreements that we might actually disagree with. The long, often difficult-to-read, all-caps legal regurgitations seem like they are asking not to be read. Even the most ambitious among us may give up on the miles-long sentences when a picture, game or useful tool is only a click away. Or we might lack the law degrees needed to truly understand what we are signing up for.
The browser add-on Terms of Service: Didn’t Read offers a partial solution by reading these texts, making them more digestible and explaining the ramifications, thereby helping us to retain data in certain cases. But the ultimate responsibility to read these terms and to decide what we agree and do not agree with lies solely with us.
Major impact with minor time investments:
A few additional measures can help limit what individual online service and app providers know about you. Two important approaches are diversification, which helps you reduce the amount of information you share with an individual provider, and obfuscation, which is “the addition of ambiguous, confusing, or misleading information to interfere with surveillance and data collection projects.”
An easy way to start diversifying is to create throwaway email accounts, i.e., a single-use email address. Why would you want to give McDonald's your real name and email address just to use its WiFi for a few seconds? Instead, make use of one-time email address providers like Mailinator and Guerillamail. You do not have to register with them. You simply put down any email address with an invented nickname and the provider’s extension, e.g., spam(at)grr.la.
It may also make sense to set up multiple email inboxes. Should you want to hide your real name and main email address, but still receive updates or newsletters, consider using one or two aliases, i.e., email accounts that you use only for such purposes. If you want your main account to receive the emails going into your new inbox, set up a forwarding system. You can also work with Blur, whose add-on can hide your real emails (or even phone and credit cards in the premium version) – but then again, you need to trust the provider in order to allow it to protect your data.
If you are concerned about email privacy, you might want to use privacy-conscious email services such as Riseup or Mailbox. Many of these services allow you to create several aliases so that you can send emails or sign up for newsletters from different email addresses, but still read responses in the same inbox.
In addition, you can receive and send email through an email client such as Thunderbird. Not only does this allow you to use end-to-end encryption (more on this below), but it also helps you not to forget to log out of your Google, Yahoo or Microsoft accounts after writing emails, so as not to invite tracking.
Working with email clients is the most reliable way to use email end-to-end encryption, although Mailvelope, for instance, also offers encryption for major webmail providers via Chrome and Firefox add-ons. The idea of “end-to-end” encryption is simply this: communication can only be read at one user’s end and the other’s, without anybody in between (i.e., your internet provider, or intelligence agencies with access to its servers) being able to read or tweak your messages. The most widespread way to encrypt email communication is “PGP,” which stands for “pretty good privacy” (as already said, online privacy is never perfect).
To find out who in your community is already using PGP encryption, search for their name or email on a public key mail server such as MIT’s. Typically, the same add-ons that enable end-to-end encryption also allow you to sign your emails digitally. That would be like sealing your letters with a wax emblem. When trying out end-to-end encryption, you may soon find that it is not the easiest to use and takes some getting used to.
Depending on your needs and wants, end-to-end encryption may be worth the effort. Again, even if we have “nothing to hide,” there may be things we don’t want others to read, or have the option to read. Take a look at this longer guidebook (Mac, Windows), and install the appropriate tools to start working with end-to-end encryption.
There are some easier ways to use encryption – for example, the program Mynigma, a new email client developed by a Berlin-based startup. It ensures end-to-end encryption of communication between you and other Mynigma users. Alternatives with default end-to-end encrypted email messaging include the Switzerland-based Protonmail and the German startup Tutanota.
With all these programs, however, your emails are only encrypted when you communicate with other users of the same service. With that in mind, the encryption tool Pretty Good Privacy (PGP) is the most ideal, as it is the most widely used email encryption tool.
There are other modes of diversification to consider. A starting point is online search. One method of diversification is to use some of the most popular alternatives to web searches, such as DuckDuckGo, Ixquick and Startpage (they all have easy-to-use browser add-ons). The latter two websites are provided by the same company and take your search request anonymously to services like Google and return the findings to you.
Another convenient tool is the add-on Disconnect Search, which lets you pick your favorite search engines and displays the results that these engines would show, while anonymizing your search.
There are many different providers that enable online collaboration – for example, Thinkfree and Zimbra. To share notes online or co-edit texts, Etherpad and Piratepad offer easy-to-use and anonymous solutions.
For sharing files, consider more privacy-conscious alternatives like Spideroak and TeamDrive. These services encrypt data before they leave your computer, so that even the providers themselves do not have access to your data unless they have access to your computer. Onionshare, which takes more effort to set up, goes a step further and provides full anonymity, should you want to share files with friends or colleagues.
If you want to further diversify your online activity, consider using different map tools like Open Street Maps, an open source tool curated by the “crowd,” i.e., volunteers who contribute out of conviction rather than for money. And why not use your local public traffic provider’s homepage if you need to figure out a train connection?

Privacy and security are interrelated. In fact, they build on each other: poor computer security puts your privacy at risk. You can take simple steps to increase your computer security and to ensure that the data on your computer and phone are secure from intruders.
For starters, follow the “single most important [measure] for everyday computer users”: Keep your software up to date, i.e., regularly install all updates. You can even set auto-update as a default.
Next, especially when using open networks (i.e., not your work or home network with a password-protected router), you should remember to use a firewall that protects malicious “packets” from having access to your computer. Running your firewall usually doesn’t come at high performance costs, so you can have it running at all times. Here are some pros and cons, for Mac and Windows.
Encrypting your email messages protects your communication, but to protect data saved on your computer, you can also encrypt your hard drive. It’s easier than it sounds, and both Apple and Microsoft offer relevant advice. Encrypting your hard drive does not come with performance costs and is especially important if you often use your computer away from home. If you only protect your computer with a password, but do not encrypt your hard drive, a criminal could simply remove the drive from your computer and then read all the content.
If you think it's unnecessary to encrypt all your files, you can choose to encrypt single folders – for example, those containing your bank statements or diary (Mac, Windows). This is also useful when using cloud services, for even if you use trusted services like those mentioned earlier, your data is doubly secure if you encrypt them before uploading. Backing up your data is strongly encouraged, especially if you often use your laptop outside of home. Cloud services make this easier, but many people still work with hard drives, doing backups manually or with the help of a program like Time Machine on Mac. Some people use laptop-tracking software to determine the location of their stolen or lost laptop.
Highly recommended investments of your time:
Passwords are important for both online security and privacy. Bad passwords can easily nullify most of your other efforts. Here is some basic advice on choosing passwords: Don’t use the same password across devices. Don’t use your name or account in the password. Don’t use common passwords (e.g., “12345,” family names). Strong passwords are long and include a combination of lower- and uppercase letters, numbers and special characters; their strength increases with length and complexity.
To test your password, you can play around with the “How secure is my password?” tool. This site will calculate how quickly a desktop PC could crack your password. “Hello12,” for example, would take about 19 seconds. But caution: after you enter your password into this public site, it might not be a bad idea to change it. And if you really believe that you are up against advanced adversaries, keep in mind that they’ll have much more computing power than a normal desktop PC.
If you want to be serious about passwords, you should consider getting a password manager, which is considered to be the most secure way to use complex and varying passwords and still remember them. KeePassX is an open-source password manager, and once you’ve set your master password, it creates and saves passwords for you. To enhance convenience, you can synchronize your password database – for example, by using a cloud service, so that you have access on various computers as well as your phone. That way, you’ll have ’round-the-clock access to strong passwords.
Alternative password managers include LastPass, 1Password and the recently developed, open-source Encryptr. Depending on your environment, you can also consider breaking one of the most basic rules: write it down. By this, we don’t mean, “Write it down and pin it to your computer.” But unless you believe that somebody will break into your room to filch your password, why not write it down on a sheet of paper and slip it into a random folder? If you don’t write it down, you may be wary of choosing a highly secure password, for fear of forgetting it.
If you don’t want to use a password manager, but you’re interested in strengthening your passwords, check out these detailed tactics and background information.
For passwords that don’t protect your most important assets, you can develop your own password algorithm, or a logic by which you invent passwords that only you can follow. The goal is to be cryptic to everyone but you, using patterns, repetition and ideas particular to you.
To create a strong password that is nevertheless easy to remember, you could take ideas that you know well, such as your mother’s name (let’s call her Alice), her birthday (let’s make it November 3, 1955) and her favorite color (let’s make it green) to create the following: 03_Alice_11_Green_55. If you throw in some special characters, the password would become even harder to crack: 03_Alice?_11_Green!_55.
On the topic of special characters: be aware that most hackers or password-cracking tools know full well that many people replace “a” with “@” and “e” with “3.”
Password patterns can allow you to use very different but related phrases for all of your accounts, basing one off of the other. For example, if you use your mother’s birthday, you could use your dad’s, brother’s, grandmother’s or dog’s for other accounts. Repeating patterns will make your passwords easy to remember, though it can put you at risk if an adversary gains access to multiple passwords and recognizes the patterns. And, of course, any pattern model becomes ineffective as soon as it is written or suggested anywhere online (so never use the one we just suggested).
Finally, take advantage of online services that offer two-factor authentication. These programs require not only a password, but also, say, a code sent to you in a text message. You input the code to verify that you are indeed the person trying to access the account. Google, Twitter and Dropbox were the first to offer this procedure. Here is a comprehensive list of websites that offer this service.

At this point, it is almost impossible to secure your smartphone as much as your computer because you have much less control over the software of the former. But your phone is always with you, and you use it for highly personal purposes.
A smartphone is the best example of the tempting comfort and utility of online connections: the more apps you possess, the easier it is to share content and connect with people on a variety of platforms. At the same time, the more you use these apps, the more data you provide external actors. And the more information about yourself you save on your smartphone, the higher the privacy implications, should it get stolen.
For an exemplary overview of data misuse, check out the web-based Androlyzer database, which collects reports on Android’s violations of user privacy and lapses in device security. If you don’t think this is relevant, consider the fact that 40 percent of adulterous divorce cases in Italy use WhatsApp as evidence of unfaithfulness.

To protect online traffic on your smartphone, you can take steps similar to those mentioned earlier in regards to your computer. For anonymous browsing, use Orweb (Android) or the Onion browser (iOS), both of which are based on Tor. There are also more user-friendly browser apps that do not retain online traffic and offer increased privacy settings; here are suggestions for Android and iOS.
Similarly, you can use VPN clients for your phone; the functionalities are similar to those for computers. In fact, many of the aforementioned VPNs cover your phone without additional charge. We recommend you look at the above-mentioned list of VPNs, but here are some more options for VPNs that are available for Android or iOS.
The Open Whisper Systems open source app Signal enables end-to-end encryption of your calls and messages, automatically and conveniently. It is recommended by most IT experts. There are alternatives such as Silent Phone for encrypting phone calls or Threema for securing messages. You can compare these services in the EFF’s Secure Messaging Scorecard. In addition, Chat Secure and OTR (off-the-record) messaging services secure your online chats, and the iPGMail app brings PGP encryption to your iOS device.

As with your computer, you can diversify your apps to avoid having one provider gather all sorts of data about you. You have already done so if you started using the aforementioned communication apps. DuckDuckGo and Disconnect Search also exist for mobile phones. Various alternatives to Google or Apple Maps exist for both Android and iOS, although you need to pay for some of them. You can also consider using your local public transportation provider’s apps, or use BBBike as a bike-route planner.
When browsing the web on your phone, keep in mind that most browsers enable cookies by default. Here is an overview of how to change these settings. The company AdBlock Plus offers a mobile browser that blocks all advertisements, and Apple has allowed ad blockers in the newest version of iOS. As mentioned before, advertisements might not only annoy you, but also deliver malware and often drastically increase the use of your mobile data. Finally, this website will tell you whether your mobile carrier is tracking the websites you visit on your phone.
It is advisable to encrypt your phone’s hard drive (Android, iOS). This also offers extra security in case you lose your phone. Finally, remember to thoroughly delete all your data when you give your phone away (Android, iOS). Should you be worried about your phone being stolen, you can download apps that remotely track and delete data (Android, iOS).
Next, you should think about the way you use your location services. Apps that make use of your locations services can be very useful. Nevertheless, your location – especially your location history – can be extremely revealing and is among your most private information.
Most of us would not agree to carry personal tracking devices, yet we voluntarily take our phones everywhere with us. A variety of apps on your phone, a range of Mobile Location Analytics (MLA) companies and your network provider can constantly track you unless you take active measures to prevent them from doing so.
Turning off your location reporting for apps and deleting your history are some of the most basic steps you can take, and both Android and iOS offer useful solutions. However, it is trickier with MLA companies: they use your device’s WiFi and Bluetooth signals to identify your phone’s unique MAC address (though not your phone number), and they track your location with a broad network of hotspots. You can opt out of some of these companies – which include airports or hotels – but not from all of them, unfortunately.
It can be similarly difficult to prevent your network provider from tracking you. In both cases, the best solution is to turn off your WiFi, Bluetooth and mobile networks when you don’t use them, or to put your phone into a Faraday cage like Offpocket, which blocks all radio signals coming in or out of your cellphone. But the obvious downside: your phone won’t be connected anymore, rendering it useless for many activities. Still, if you are serious about protecting yourself, check out Tactical Tech’s resources on mobile- and smartphones.
Just as the internet has propelled economic growth and enhanced freedom in a variety of ways, the use of data offers a wealth of possibilities. But most of us remain unaware of how such data can be used, and we do not always consent to the use of our information. More and more of our personal information is becoming available in conjunction with more and more ways of saving data cheaply and easily – a situation laden with risks.
To properly determine what we want the future use of data to look like, we need to be able to judge risks as well as potential benefits. With that in mind, this guide seeks to provide users with a starting point for greater awareness of online privacy and security, and to help each of us to conduct such an assessment.
The authors, Mirko Hohmann and Rahel Dette, would like to thank Isabel Skierka, Marc Becker and Balint Balazs for their research and writing support.
For more information and feedback, please contact Mirko Hohmann via email or on Twitter (PGP key fingerprint: 7C3A C2FE 90B5 208B 38A1 5713 1577 AE41 B022 E22D).
Disclaimer: External links are provided as a convenience and for informational purposes only; they do not constitute an endorsement or approval by GPPi of any of the products, services or opinions of the corporation, organization or individual. GPPi bears no responsibility for the accuracy, legality or content of the external site or of subsequent links. Contact the external site for answers to questions regarding its content.
To allow for broader use, this work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 3.0 International License.